TLDR:TITAN(Threat Intelligence Tracking via Dynamic Networks), is an AI-driven cybersecurity solution from Microsoft that uses a dynamic threat intelligence graph to provide real-time insights and proactively disrupt cyber threats. Its guilt-by-association techniques uncover hidden threats, allowing security teams to prevent attacks before they occur, resulting in significant improvements in threat detection and disruption efficiency.
In the face of an increasingly complex and dangerous digital landscape, cyberattacks present a formidable challenge to organizations worldwide. As attackers continually refine their tactics, traditional security measures struggle to keep up. Recognizing this critical issue, Microsoft has pioneered TITAN, an innovative solution that leverages Artificial Intelligence (AI) to enhance threat intelligence and proactively counteract cyber threats.
A Real-Time, Adaptive Approach to Threat Intelligence
TITAN employs a dynamic, time-evolving threat intelligence (TI) graph that integrates telemetry from both first and third-party sources, such as Microsoft Defender for Threat Intelligence, Microsoft Defender for Experts, and a unified security operations platform. This graph is continuously updated, offering security teams real-time insights into emerging threats.
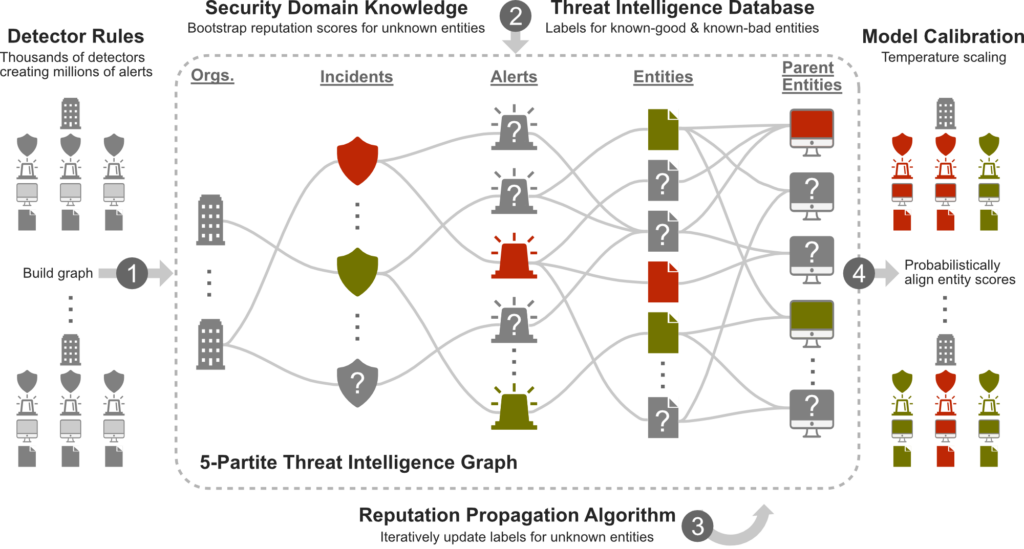
The TITAN architecture includes four key stages: (1) creating a graph from telemetry data collected by 1st and 3rd party detectors within the Unified Security Operations Platform, (2) incorporating threat intelligence from Microsoft’s resources, (3) leveraging reputation propagation algorithms to identify unknown entities as benign or malicious, and (4) refining reputation scores for all entities within the graph.
Key features of the TITAN graph include
- Real-time updates: The graph refreshes every hour, ensuring that security teams have access to the latest threat intelligence.
- Edge weights: Relationships between entities in the graph are denoted by edges with assigned weights that indicate their strength. An edge weight decay function prioritizes newer relationships by automatically diminishing weights based on the age of the relationship.
- Pruning: The graph systematically removes outdated nodes and edges, maintaining its relevance and operational efficiency.
Guilt-by-Association: Exposing Hidden Threats
At the heart of TITAN’s efficacy is its implementation of guilt-by-association techniques. This methodology scrutinizes the relationships between entities within the TI graph to uncover previously unidentified malicious infrastructures. By connecting seemingly benign entities to recognized malicious ones, TITAN can reveal hidden threats before they are exploited in attacks.
TITAN’s guilt-by-association approach utilizes semi-supervised label propagation, a technique that iteratively assigns reputation scores to nodes based on the scores of their neighboring entities. This iterative process continues until the scores stabilize, yielding high-confidence reputation scores for each entity within the graph.
Preventing Attacks Before They Occur
While traditional security systems often depend on reactive strategies responding to threats post-incident TITAN empowers security teams to adopt a proactive stance, thwarting attacks before they can inflict damage.
For instance, if TITAN identifies unusual activity from an IP address that appears benign but is linked to known malicious domains, it will elevate the reputation score of that IP address. This elevation triggers detection and disruption protocols, effectively neutralizing the threat before an attack can initiate.
Measuring TITAN’s Success
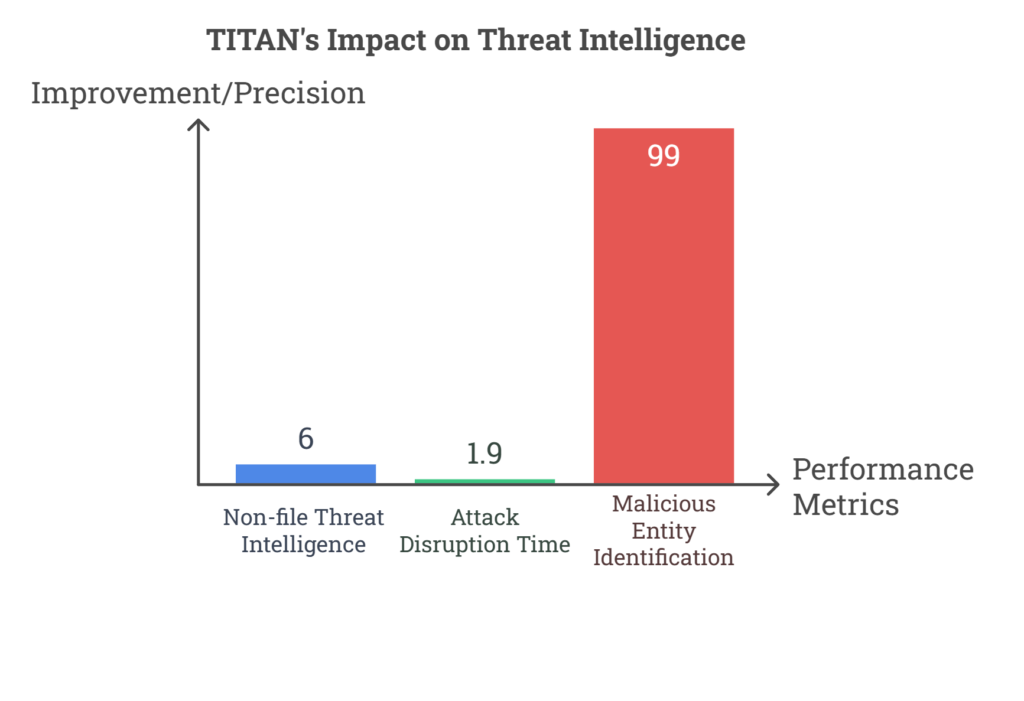
Since its implementation, TITAN has shown remarkable success in enhancing threat intelligence and disruption capabilities. Key outcomes include
- A 6x increase in non-file threat intelligence.
- A 1.9x reduction in the time taken to disrupt attacks.
- 99% precision in identifying malicious entities.
These results underscore TITAN’s capability to proactively safeguard organizations against cyber threats.
Conclusion
TITAN signifies a notable advancement in the realm of cybersecurity defenses. By harnessing the power of AI and a dynamic, real-time threat intelligence graph, TITAN equips security teams to:
- Identify and neutralize malicious activities at scale.
- Expose hidden threats through guilt-by-association techniques.
- Prevent attacks before they materialize, thereby minimizing potential harm.
As cyber threats continue to evolve, innovative solutions like TITAN are crucial for ensuring a secure digital environment. Microsoft’s ongoing dedication to developing state-of-the-art security solutions such as TITAN instills optimism for a more secure future.
Source: TITAN Architecture Paper, Microsoft Threat protection Blog.